We Meaicon digitail security service provider securing digital ecosystems and value chains across the world. We delivers a comprehensive portfolio of next-gen security services to mitigate everyday risks across the network, cloud, and mobile devices.
We function as a strategic security partner for enterprises across the region to implement zero-trust security principles, automate identity and access management, identify and remediate risks and simplify compliance management. Our Security Expertise (Scalable. Adaptive. Proven)
Innovative solutions to design & implement a solid (IAM) roadmap for the future.
Automate tasks and transform the way you manage, monitor and control access and identity privileges. Leverage our capabilities to drive IAM programs through robots to automatically generate IAM system configurations and manage digital identities at scale.
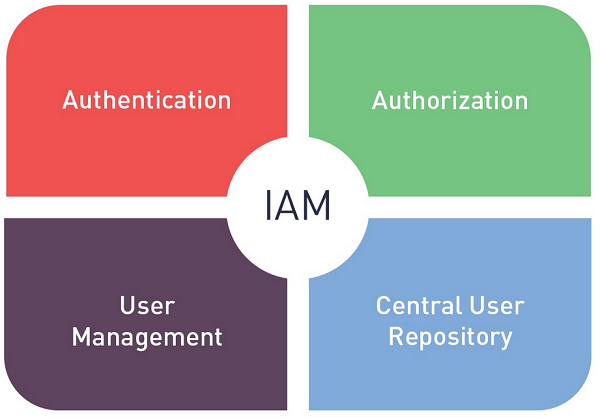
Proactively address security flaws to meet compliance needs. Transform legacy IAM solutions to make them risk-aware. Strengthen access governance. Enhance visibility of identities across businesses.
Secure digital access for external users across digital channels. Build customer trust through seamless omni channel experiences. Control consumer access to apps, systems, and services. Enable your business with effective consumer interactions.

On-demand security testing services for deep dive cyber defense evaluation

For simulating various combinations of threat scenarios to test cyber defense capabilities in a safe, real-time environment. Evaluate your security team's capabilities to take on sophisticated attacks and optimize the effectiveness of security controls.
Consumption-based security assessment services to quickly provision or de-provision resources based on your testing needs such as architecture risk analysis, threat modeling, penetration testing & vulnerability management.

Review security strategy, including IAM, cloud-native & security tools, workloads, applications, architecture, and connectivity. Identify to-be state, find improvement areas, and provide recommendations. Define cloud security strategy aligned with regional and organizational compliance requirements. Prioritize projects based on cost, effort, and risk.

Identify compliance requirements, drive workshops to understand the status quo. Conduct risk assessment using CSA, CIS, and cloud-native security checklists such as AWS. Evaluate remediation options across engineering, architecture, and technology, IAM, security testing, development (CI/CD), and operations (DevOps). Evaluate cloud assets including, compute, storage, databases, networks, containers, boundaries, security technologies.

Architecture design, cloud-native and non-native technologies, and configuration. IAM configurations, roles, users, secrets, and key management. Enterprise directory, IAM integration, DevSecOps automation. Integration of continuous security testing, continuous compliance, protection, and monitoring tools. Security in Infrastructure as Code (IaC - terraform) and configuration management scripts (Chef, Puppet, Ansible). Bespoke integration with applications and systems using API.

Support shift-left development paradigm. Develop security test scripts for CI and CD platforms like Jenkins, Bamboo, & Circle CI. Integration with commercial and open source security tools such as Arachni, Gauntlt, NMap, Burp, Fortify, Checkmarx, Coverity, Black Duck, Flexera, Rapid7, Tenable/Nessus, TwistLock, & Inspec.io. Develop security tests that balance performance and security. Ensure security feedback to help developers build secure code.

Integration of IAM and PAM solutions, MFA (email, text, authenticators), and SSO. Integration/extension of enterprise and cloud directories and IAM solutions. Role-based and attribute-based access control and SAML/OpenID Auth integrations. Extension of IAM solution to support micro services, containers and cloud-native solutions. Develop scripts for Infrastructure as Code (IaC) and Configuration management tools such as Terraform, Cloud Formation, Chef, and Puppet to build security guardrails for computing, storage, containers. Develop automation for security testing of cloud assets. Auto integrate cloud assets into management, monitoring platform. Security operations automation and integration with CMDB, ticketing, and GRC platforms.

Establish a business-aligned data protection framework for cloud and SaaS-based storage. Define data protection processes and guidelines. Define technology selection and implementation roadmap for securing buckets and blobs, cloud SQL and NoSQL DB, & long-term storage. Secure access using both cloud-native IAM and enterprise integrated IAM/PAM, SSO, MFA, encryption, and anonymization. Promote awareness of data protection, identify owners, and custodians. Monitor, manage & enhance data protection technologies through cloud-native and non-native security technologies, including Cloud DLP & native access logs.